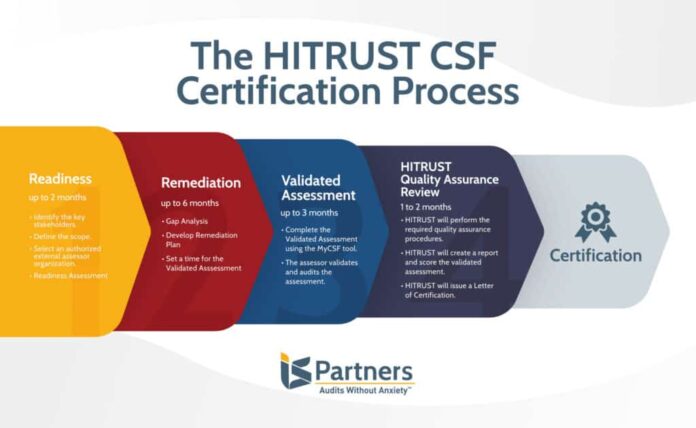
The Hitrost Framework is an information security framework designed to cover all the important areas related to information assurance. An all-encompassing integrated HITRUST framework encompassing governance, compliance, trust, and cyber security. Designed by information security experts in collaboration with major information assurance stakeholders, the HITRUST corpus describes a set of rules and metrics that enable organizations to identify, address, and prevent a range of security threats. One of the biggest problems in today’s information security environment is how to find a comprehensive solution to the many challenges facing this ever-changing area. Organizations may adopt one approach or the other but cannot ensure that their decision-making process is consistently informed and well-informed.
There are six components of the HITRUST framework that are designed to address issues specific to GRC certified enterprise software. These are Operational, Processes, Models, Audiences, and Resources. To this end, there are two alliance partners that have been strategically placed to provide continuous enhancement to the HITRUST project. CISA and GCS are the software design organizations that are implementing the framework on behalf of the alliance partners. CISA is the North American Information Security Management Association (NISA) and GCS is the Global Certification Council for Standards (GCCS).
The operational requirements of the HITRUST framework build on an organizational understanding of how a company can assess its own internal processes as well as those of external influences such as government and external threats. The operational specifications of the HITRUST foundation to build on this understanding by describing the development of a generic security framework that can be used by all the business components to build an internal security system that meets the specific requirements of the organization. The trust assessment process starts with a security definition that provides a description of the security system requirements. It then proceeds to develop an implementation plan that specifies the steps required to meet the security objectives of the organization.
The trust framework then describes the operations necessary to define the architecture of the information protection program. This architecture is typically composed of the infrastructure and the application. Both are operational in nature and each has an Information Protection Standard (IP Standard) domain that define the operation of the application in terms of security controls. In most cases, the implementation plan also specifies the security controls that are functional in the application domain.
The data protection requirements of the trust framework assume that the environment is controlled to protect sensitive information from unauthorized access. This means that there are at least two environmental security controls. The first is the physical environment, which includes physical hardware and software that are needed to implement the security measures. In addition, the information must be protected against loss, theft, damage, or vulnerability. The second environmental security control is performed at the logical level by controlling access to the information that resides on the software. The physical environment requires dedicated hardware and includes isolation from other hardware that can influence the integrity of the software and the integrity of the hardware.
Read more: What is Hitrust MyCSF?
The requirements of the trust framework also describe a centralized view of the entire protection process. This centralized view then refers to the requirement for authorization that is used by the internal operations and the application in general. The authorization requirement therefore describes the need to gain access to all information at the enterprise level. It also describes the level of access necessary for the internal operations to be effective and economical. When evaluating this requirement, it is important to note that there are times when the requirements may call for a more restrictive level of access than what is described here.
An important aspect of the information security requirements of the trust framework is the definition of the environment that the application resides. This environment is typically one that is based on the business rules that define the functionality and the access levels that are necessary to implement the framework in the organization. For example, in a government agency, the framework might require certain regulations and restrictions to be put into place in order to ensure the privacy of the health information of the citizens that are a part of the agency. In this case, the organization would have the framework in place that enforces the regulations.
Another aspect of the trust framework deals with incidents and potential incidents. In the event that the information protection program or the enterprise network experiences an incident, the trust framework will take the incident and look for measures that will help reduce or stop the problem. In essence, the trust framework acts as a discipline for organizations that help to moderate the risks. In the event that the organization doesn’t respond quickly enough to stop an incident from becoming a major issue, there could be a major backlash against the organization. Therefore, organizations that are serious about having a trust framework must be willing to implement the disciplines that help to moderate and contain the risks that can result from having an incident response program in place.